A DNS root server is a critical component of the Domain Name System (DNS), the hierarchical and decentralized naming system used to identify computers, services, and other resources reachable through the Internet. The primary function of a DNS root server is to respond to DNS queries for the root zone, which is the top-level domain (TLD) in the DNS hierarchy.
Role and Function of DNS Root Servers
- Resolution Process Initiation:
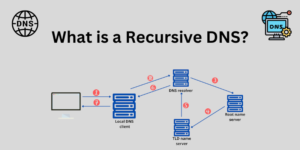
- When a user types a domain name (like www.example.com) into their browser, the request is first sent to a local DNS resolver.
- If the local DNS resolver does not have the information cached, it forwards the query to a DNS root server.
- The DNS root server does not have the specific IP address of the requested domain but responds with the addresses of authoritative servers for the appropriate top-level domain (e.g., .com, .org, .net).
- Distribution of Authority:
- The DNS root servers direct the query to the appropriate TLD name servers. For example, if the query is for www.example.com, the root server will direct the query to the .com TLD name servers.
- These TLD name servers then provide the IP address of the authoritative DNS server for the specific domain (example.com).
Structure and Operation
Hierarchical Structure
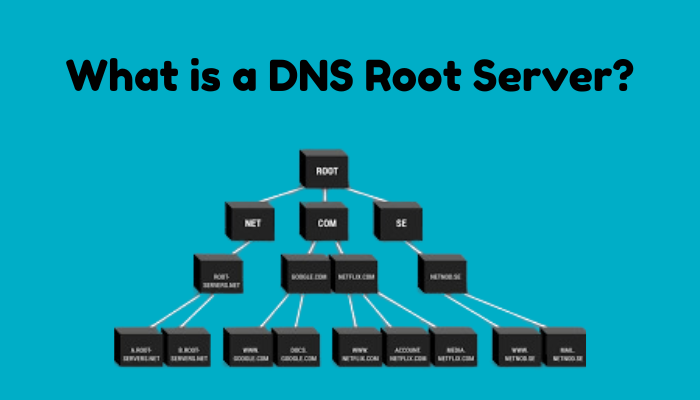
- Root Zone:
- The root zone is the top-level DNS zone in the hierarchical namespace of the DNS.
- It contains pointers to the authoritative name servers for all TLDs, such as .com, .org, .net, and country-code TLDs like .uk and .jp.
- Authoritative Servers:
- Each TLD has its own set of authoritative name servers which manage the records within their domains.
- The DNS root servers act as a directory for these TLD servers.
Global Network of Servers
- Thirteen Root Server Clusters:
- There are 13 root server clusters identified by the letters A to M.
- These clusters are operated by different organizations around the world, ensuring redundancy and reliability.
- Each cluster can consist of multiple servers, often distributed globally, to ensure robustness and availability.
- Anycast Technology:
- Anycast routing is used to distribute the DNS root servers across many geographical locations.
- This allows queries to be answered by the nearest available root server, enhancing speed and reliability.
Organizations Managing DNS Root Servers
- ICANN (Internet Corporation for Assigned Names and Numbers):
- ICANN oversees the allocation and management of domain names and IP addresses.
- It coordinates the global DNS root server system, working with various operators to ensure stability and security.
- Root Server Operators:
- Different organizations manage the 13 root server clusters, including academic institutions, government agencies, and private companies.
- Examples include VeriSign (managing the A and J root servers), the University of Maryland (managing the D root server), and NASA (managing the E root server).
Importance of DNS Root Servers
- Internet Stability and Performance:
- DNS root servers are crucial for the stability and performance of the Internet.
- They provide the necessary information to route queries efficiently across the DNS hierarchy.
- Security and Integrity:
- Maintaining the security and integrity of DNS root servers is vital to prevent DNS-related cyber-attacks.
- Measures such as DNSSEC (DNS Security Extensions) are implemented to protect against threats like cache poisoning.
Why Are There Only 13 DNS Root Server Addresses?
The existence of only 13 DNS root server addresses is rooted in historical, technical, and practical considerations. These factors include the limitations of the early Internet infrastructure, the design of the DNS system, and the need for efficiency and reliability. Here’s a detailed explanation of why there are only 13 DNS root server addresses:
Historical and Technical Background
- Early Internet Constraints:
- When the Domain Name System (DNS) was first developed in the 1980s, the Internet infrastructure was far less advanced than it is today.
- Memory and processing power were limited, necessitating efficient use of resources.
- Protocol Limitations:
- The DNS protocol, as specified in the original Request for Comments (RFC) documents, needed to ensure that responses could be transmitted within a single User Datagram Protocol (UDP) packet.
- UDP packets were limited to 512 bytes. Given this constraint, only 13 root server addresses could fit within this size limit, along with necessary overheads.
Design and Implementation Considerations
- Single UDP Packet Response:
- The decision to limit the number of root server addresses to 13 ensured that the entire list could be included in a single DNS response.
- This design choice optimized the speed and efficiency of DNS queries, as splitting the response across multiple packets would have added complexity and latency.
- Root Hints File:
- The root hints file, which is used by DNS resolvers to locate the root servers, includes these 13 addresses.
- Keeping this file concise and manageable was another reason for the limitation, simplifying updates and distribution.
Practical and Operational Factors
- Redundancy and Reliability:
- Each of the 13 root server addresses represents a root server cluster rather than a single machine.
- These clusters employ Anycast technology, which allows multiple geographically dispersed servers to share the same IP address, ensuring redundancy and reliability.
- Load Distribution:
- Anycast routing ensures that queries are directed to the nearest available root server, balancing the load and enhancing performance.
- This setup allows the DNS root server system to handle the vast number of queries it receives efficiently.
Security and Management
- Simplified Management:
- Limiting the number of root server addresses simplifies the management and coordination among the root server operators.
- It ensures that updates and changes can be more easily implemented and propagated.
- Security Considerations:
- A smaller number of root server addresses reduces the attack surface, making it easier to secure the DNS root server system.
- The root server operators implement robust security measures to protect against threats such as Distributed Denial of Service (DDoS) attacks.
Organizational and Policy Aspects
- Diverse and Decentralized Management:
- Different organizations, including academic institutions, government agencies, and private companies, operate the 13 root servers.
- This decentralized approach enhances the security and resilience of the DNS system.
- ICANN Oversight:
- The Internet Corporation for Assigned Names and Numbers (ICANN) oversees the DNS root server system, ensuring that it remains stable, secure, and interoperable.
- The collaborative effort among ICANN and the root server operators ensures that the system adapts to evolving technological and security needs.
How Do Resolvers Find DNS Root Servers?
DNS resolvers, also known as DNS clients or recursive resolvers, play a crucial role in translating human-readable domain names into IP addresses. To do this, they must know how to find DNS root servers. Here’s a detailed explanation of how resolvers accomplish this task:
Initial Configuration: The Root Hints File
- Root Hints File:
- Every DNS resolver is initially configured with a root hints file, which contains the IP addresses of the 13 DNS root server clusters.
- This file is included with the resolver software or can be downloaded from trusted sources like the Internet Corporation for Assigned Names and Numbers (ICANN).
Process of Finding DNS Root Servers
- Bootstrapping Process:
- When a DNS resolver starts up, it reads the root hints file to obtain the IP addresses of the root servers.
- These addresses are used to initiate the DNS resolution process.
- Recursive Query Process:
- When a user queries a domain name, the resolver first checks its local cache to see if it already has the answer.
- If the information is not cached, the resolver sends a query to one of the root servers listed in the root hints file.
- The query typically looks for the authoritative name server for the top-level domain (TLD) of the requested domain (e.g., .com for www.example.com).
- Root Server Response:
- The contacted root server responds with a referral to the TLD name servers for the appropriate domain.
- The resolver then queries these TLD name servers to get the authoritative name server for the specific domain.
Maintaining and Updating Root Hints
- Regular Updates:
- Although the root server IP addresses rarely change, resolvers should periodically update their root hints file to ensure they have the latest information.
- ICANN and other authoritative sources provide updated versions of the root hints file.
- Automatic Updates:
- Some modern DNS resolver implementations include mechanisms to update the root hints file automatically.
- These updates can be fetched over the Internet from trusted sources, ensuring that the resolver always has current root server information.
Resilience and Redundancy
- Anycast Technology:
- The root server addresses listed in the root hints file use Anycast routing, meaning multiple servers around the world share the same IP address.
- This ensures that DNS queries are directed to the nearest or most responsive server, enhancing speed and reliability.
- Failover Mechanisms:
- If a resolver fails to receive a response from one root server, it will try another server from the root hints file.
- This redundancy ensures that the resolver can always contact a root server, even if some servers are unreachable.
Security Considerations
- DNSSEC (DNS Security Extensions):
- DNS resolvers often use DNSSEC to validate responses from root servers.
- DNSSEC provides cryptographic assurance that the received DNS information has not been tampered with.
- Trust Anchors:
- Resolvers can be configured with DNSSEC trust anchors, which are cryptographic keys used to verify the authenticity of DNS responses starting from the root zone.
What Happens if a DNS Root Server Becomes Unavailable?
The DNS (Domain Name System) infrastructure is designed to be robust and resilient, ensuring that the Internet continues to function smoothly even if one or more DNS root servers become unavailable. Here’s an in-depth explanation of what happens in such a scenario:
Redundancy and Distribution
- Thirteen Root Server Clusters:
- There are 13 DNS root server clusters, each identified by a letter from A to M.
- Each cluster consists of multiple servers distributed globally using Anycast technology.
- Anycast Technology:
- Anycast routing allows multiple servers to share the same IP address.
- When a DNS query is made to a root server IP address, the Anycast network routes the query to the nearest or most responsive server.
Impact of Root Server Unavailability
- Query Redirection:
- If a specific root server becomes unavailable, Anycast routing automatically redirects DNS queries to the next closest server in the same cluster.
- This means that other servers will still answer queries intended for an unavailable server in the same cluster.
- Redundancy Across Clusters:
- Since there are 13 independent root server clusters, the failure of one or even several clusters does not significantly impact the overall DNS resolution process.
- DNS resolvers are programmed to query multiple root servers and can switch to another server if one does not respond.
Resilience and Failover Mechanisms
- Load Balancing:
- Through Anycast, the load is evenly distributed among the various root servers, preventing any single server from being overwhelmed.
- This distribution helps maintain performance and reliability even when some servers are down.
- Built-in Failover:
- DNS resolvers have a list of all 13 root server IP addresses from the root hints file.
- If a resolver fails to get a response from one root server, it will try the next address in the list until it successfully contacts a root server.
Maintenance and Recovery
- Regular Maintenance:
- Root server operators perform regular maintenance and updates to ensure the servers are running optimally.
- This maintenance is usually planned and coordinated to minimize any potential impact on DNS resolution.
- Rapid Recovery:
- In the event of a server failure, root server operators have protocols in place to quickly restore service.
- This can include bringing up backup servers or rerouting traffic to other operational servers within the cluster.
Security Measures
- DDoS Protection:
- DNS root servers are equipped with advanced protection mechanisms against Distributed Denial of Service (DDoS) attacks.
- These measures include traffic filtering, rate limiting, and other techniques to mitigate the impact of such attacks.
- DNSSEC (DNS Security Extensions):
- DNSSEC adds a layer of security to ensure that DNS responses are authentic and have not been tampered with.
- Even if a root server is compromised, DNSSEC can help detect and prevent the propagation of malicious responses.