What is an ip address?. Every time you use the Internet, whether to check your email, browse social media or stream a video, your device uses an IP address. An IP address, which stands for Internet Protocol address, is a unique set of numbers assigned to every device connected to the Internet. Think of it like a home address for your computer or smartphone, allowing information to be sent and received accurately.
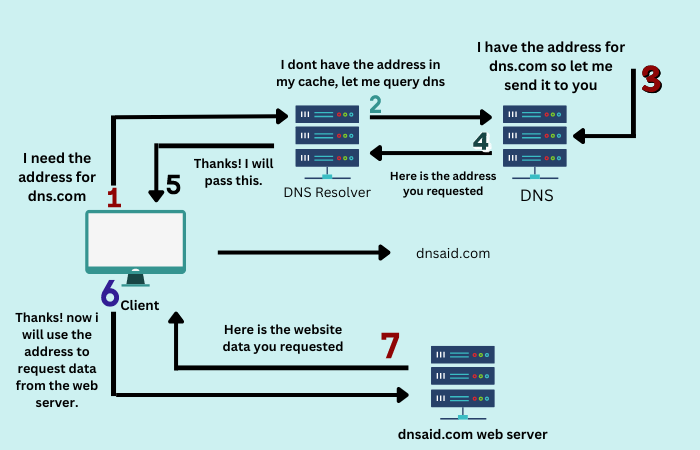
Without IP addresses, the Internet wouldn’t function as we know it. Just as you need a correct address to send a letter through the mail, the Internet relies on IP addresses to deliver data to the right place. This system ensures that emails, webpages, and other digital information reach the correct destination. Understanding IP addresses helps us appreciate the complexity and efficiency of the Internet, making our online experiences possible and seamless.
What are the Types of IP Addresses?
IP addresses come in various types, each serving different purposes in the digital landscape. Understanding these types is crucial for grasping how the Internet works. Here, we will explore the primary types of IP addresses: IPv4, IPv6, static, dynamic, public, and private IP addresses.
IPv4 (Internet Protocol version 4)
Structure: IPv4 addresses are 32-bit numbers, typically represented in a dotted-decimal format consisting of four numbers separated by periods (e.g., 192.168.1.1). Each number can range from 0 to 255.
Example: An IPv4 address might look like 192.168.0.1.
Usage: IPv4 has been the backbone of the Internet since its inception. With approximately 4.3 billion unique addresses available, IPv4 has supported the explosive growth of internet-connected devices. However, as more devices connect to the Internet, the limitations of IPv4’s address space have become apparent, leading to the development of IPv6.
IPv6 (Internet Protocol version 6)
Structure: IPv6 addresses are 128-bit numbers, represented in hexadecimal format and separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
Example: An IPv6 address might look like 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
Why IPv6?: IPv6 was developed to address the limitations of IPv4, providing an almost inexhaustible number of unique addresses. It supports a vast number of devices, ensures better network efficiency, and enhances security features. As more devices connect to the Internet, the adoption of IPv6 is becoming increasingly important.
Static vs. Dynamic IP Addresses
Static IP Addresses
Definition: A static IP address remains constant and does not change over time. It is manually configured and assigned to a specific device, ensuring that the device always has the same IP address.
Use Cases: Static IP addresses are commonly used for servers hosting websites, email services, or any other online resources that need a consistent address. Businesses often use static IP addresses for their important network devices to ensure reliability and easier access.
Advantages: Consistent connectivity, easier remote access, and improved reliability for hosting services.
Disadvantages: More susceptible to security risks if not properly protected, and typically more expensive to obtain from ISPs.
Dynamic IP Addresses
Definition: A dynamic IP address is assigned by a DHCP (Dynamic Host Configuration Protocol) server and can change each time the device connects to the network. This method allows for efficient management of IP addresses within a network.
How They Work: The DHCP server automatically assigns an available IP address to a device from a pool of addresses. When the device disconnects from the network, the IP address is returned to the pool for reuse.
Use Cases: Dynamic IP addresses are commonly used for residential internet connections, where a constant IP address is not necessary.
Advantages: Cost-effective, automatically managed, and less vulnerable to direct attacks compared to static IP addresses.
Disadvantages: Less stable for remote access and services that require a constant IP address.
Public vs. Private IP Addresses
Public IP Addresses
Definition: Public IP addresses are assigned to devices that connect directly to the Internet. These addresses are globally unique and allow the device to be identified across the entire Internet.
Use Cases: Public IP addresses are used for web servers, email servers, and other services that need to be accessible from the Internet.
Advantages: Ensures global reachability and accessibility for online services.
Disadvantages: More exposed to security threats and attacks, as they are accessible from anywhere on the Internet.
Private IP Addresses
Definition: Private IP addresses are used within local networks, such as home, office, or corporate networks. They are not routable on the public Internet and are reserved for internal use.
Range: Common private IP address ranges include:
- 10.0.0.0 to 10.255.255.255
- 172.16.0.0 to 172.31.255.255
- 192.168.0.0 to 192.168.255.255
Use Cases: Private IP addresses allow devices within a local network, such as computers, printers, and routers, to communicate with each other.
Advantages: It provides a layer of security by isolating internal network traffic from the public Internet and conserves the limited number of public IP addresses.
Disadvantages: Network address translation (NAT) is required to communicate with devices on the public Internet, which can introduce complexity in network configuration.
How to Find Your IP Address
Finding your IP address is straightforward, but it can vary slightly depending on the device and operating system you are using. Below, we will cover how to find your IP address on Windows, Mac, Linux, and smartphones, as well as how to use online tools to find your public IP address.
For Windows Users
- Open Command Prompt:
- Press Win + R to open the Run dialog box.
- Type cmd and press Enter to open the Command Prompt.
- Enter the Command:
- Type ipconfig and press Enter.
- Look for the section labeled “Ethernet adapter” (for wired connections) or “Wireless LAN adapter” (for wireless connections).
- The IP address will be listed next to “IPv4 Address”.
For Mac Users
- Open System Preferences:
- Click on the Apple icon in the top-left corner of the screen.
- Select “System Preferences” from the dropdown menu.
- Select Network:
- Click on the “Network” icon.
- Choose the network connection you are using (Wi-Fi or Ethernet) from the list on the left.
- Find the IP Address:
- Your IP address will be displayed under the connection status, typically labeled as “IP Address.”
For Linux Users
- Open Terminal:
- Depending on your distribution, you can find the Terminal application in the system menu.
- Enter the Command:
- Type ifconfig and press Enter (on older systems), or ip addr show and press Enter (on newer systems).
- Look for the network interface you are using (e.g., eth0 for Ethernet or wlan0 for Wi-Fi).
- The IP address will be listed next to “init.”
For Smartphones
Android
- Open Settings:
- Tap the Settings app on your home screen or app drawer.
- Select Network & Internet:
- Tap “Network & Internet” or a similar option, depending on your device.
- Wi-Fi:
- Tap on “Wi-Fi”.
- Tap on the Wi-Fi network you are connected to.
- Your IP address will be displayed under network details.
Security Implications of IP Addresses
IP addresses play a crucial role in how devices communicate over the Internet. Still, they also have certain security implications that users should be aware of. Understanding these implications can help you take steps to protect your online privacy and security.
Privacy Concerns
- Tracking and Geolocation:
- Explanation: IP addresses can be used to approximate your geographic location. While they don’t provide exact physical addresses, they can reveal the city or region where you are located.
- Implications: This can be used for various purposes, such as targeted advertising, tracking user behavior, and potentially profiling users based on their location.
- Data Collection:
- Explanation: Websites and online services often log IP addresses as part of their data collection practices. This data can be used to analyze traffic patterns, identify repeat visitors, and improve service delivery.
- Implications: If this data is misused or falls into the wrong hands, it could be used to build detailed profiles of users’ online activities, raising concerns about privacy.
Security Threats
- DDoS Attacks:
- Explanation: Distributed Denial of Service (DDoS) attacks involve overwhelming a target’s IP address with excessive traffic, causing the target system to become unavailable.
- Implications: DDoS attacks can take websites, online services, and even personal devices offline, leading to service disruptions and potential financial losses.
- IP Spoofing:
- Explanation: IP spoofing involves manipulating the IP address in the header of network packets to impersonate another device. This technique is often used in various types of cyber attacks.
- Implications: IP spoofing can be used to bypass security measures, gain unauthorized access to systems, or disguise the source of malicious activity.
- Unauthorized Access:
- Explanation: Attackers can use IP addresses to identify and target vulnerable devices on a network. Open ports and weak security configurations can make devices susceptible to unauthorized access.
- Implications: Unauthorized access can lead to data breaches, theft of sensitive information, and the compromise of personal or corporate networks.
Security Measures
- Use of VPNs (Virtual Private Networks):
- Explanation: A VPN encrypts your internet connection and routes it through a remote server, masking your real IP address with one from the VPN provider.
- Benefits: VPNs enhance privacy by hiding your true IP address, making it difficult for trackers and attackers to trace your online activities back to you.
- Firewalls:
- Explanation: Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules. They act as a barrier between your trusted internal network and untrusted external networks.
- Benefits: Firewalls can block unauthorized access attempts, filter harmful traffic, and prevent malicious activities from reaching your devices.
- Regular Software Updates:
- Explanation: Keeping your operating system, applications, and network devices updated with the latest security patches is crucial for protecting against known vulnerabilities.
- Benefits: Regular updates help close security gaps that attackers could exploit, ensuring your devices remain secure against evolving threats.
- Network Address Translation (NAT):
- Explanation: NAT is a method used by routers to translate private IP addresses within a local network to a public IP address for internet access. This adds a layer of security by keeping internal IP addresses hidden from external networks.
- Benefits: NAT helps protect devices within a local network from direct exposure to the Internet, reducing the risk of external attacks.
What Are the Common Misconceptions about IP Addresses?
IP addresses are a fundamental aspect of how the internet functions, but several common misconceptions about them could be improved. Understanding these misconceptions can help clarify how IP addresses work and what they can and cannot do.
Misconception 1: IP Addresses Provide Exact Physical Locations
Explanation: Many people believe that an IP address can reveal an exact physical address, pinpointing a device’s location down to the street or building. While IP addresses can indicate a general geographic area, they do not provide precise locations.
Reality: IP addresses can show the city or region where a device is located but not the specific physical address. This is because IP addresses are assigned by Internet Service Providers (ISPs), and the location data often reflects the location of the ISP’s infrastructure rather than the end user’s exact location. Various factors, such as the use of proxies, VPNs, and dynamic IP addressing, can further obscure the exact location.
Example: If you look up a device’s IP address, it might show that the device is in a particular city, but it won’t tell you the specific street or building.
Misconception 2: IP Addresses are Permanently Assigned to One Device
Explanation: Another common misconception is that an IP address is permanently assigned to one device and never changes. People often think that the same IP address will always correspond to the same device or user.
Reality: Many devices use dynamic IP addresses, which are assigned by a DHCP server and can change over time. ISPs often allocate dynamic IP addresses to residential customers, meaning the IP address can change each time the device connects to the Internet or periodically after a certain amount of time. Static IP addresses, which do not change, are typically used for servers and other infrastructure that require a consistent address.
Example: Depending on the ISP’s DHCP configuration, a home computer might have a different IP address each time it connects to the Internet.
Misconception 3: Multiple Devices Cannot Share the Same IP Address
Explanation: People often believe that each device must have a unique IP address and that no two devices can share the same IP address at the same time.
Reality: Within a local network (such as a home or office network), multiple devices can share a single public IP address through a process called Network Address Translation (NAT). The router assigns unique private IP addresses to each device within the network. When communicating with the Internet, these private addresses are translated to the router’s public IP address.
Example: In a typical home network, your smartphone, laptop, and smart TV might all share the same public IP address assigned by your ISP, but each device has a unique private IP address within the local network.
Misconception 4: Knowing an IP Address is a Security Risk on Its Own
Explanation: There is a common fear that simply knowing someone’s IP address can lead to immediate security risks or cyber-attacks.
Reality: While knowing an IP address can be a starting point for malicious activities, it is not inherently a security risk on its own. Security breaches usually require more information and exploitation of vulnerabilities in the device or network. However, taking measures to protect your IP address, such as using a VPN, can enhance your security and privacy.
Example: Attackers typically need to find open ports, unpatched vulnerabilities, or weak passwords to compromise a device. Simply knowing the IP address does not provide this information.
Conclusion
IP addresses are the unsung heroes of our interconnected digital world. They serve as the essential identifiers that allow devices to communicate, enabling everything from browsing the web to sending emails and streaming videos. Understanding what an IP address is, the various types available, and the common misconceptions surrounding them helps demystify this crucial element of Internet technology.
By knowing the differences between IPv4 and IPv6, static and dynamic IP addresses, and public and private ones, you gain insight into how your devices connect to and interact with the broader Internet. Moreover, being aware of the security implications and how to protect your IP address ensures a safer and more private online experience.
Ultimately, IP addresses are fundamental to the seamless operation of the Internet. Whether you’re a casual user or an IT professional, understanding IP addresses empowers you to navigate and utilize the digital world more effectively and securely.


